Because if we don’t, no one else will!
What am I talking about?
As per last Wednesday’s article, PROCUREMENT STINKS and we just can’t deny it anymore. In a nutshell, and this is just the tip of the garbage heap:
- Case studies are ranker than expired fish in a microwave on high.
- Approximately 85% of companies are AI-washing everything.
- The Gen-AI claims that it will deliver Procurement to the enterprise are FALSE.
- Intake/Orchestration is totally useless on its own.
- Consultancies are often more in the dark than the Procurement departments they are claiming they can help.
- DEI is being misused to push agendas and sometimes to Do Extra-legal Initiatives,
But this isn’t even the worst of it!
THE REVELATOR recently conducted a poll on who do you trust, and the results were more than a little disturbing as far as I am concerned.
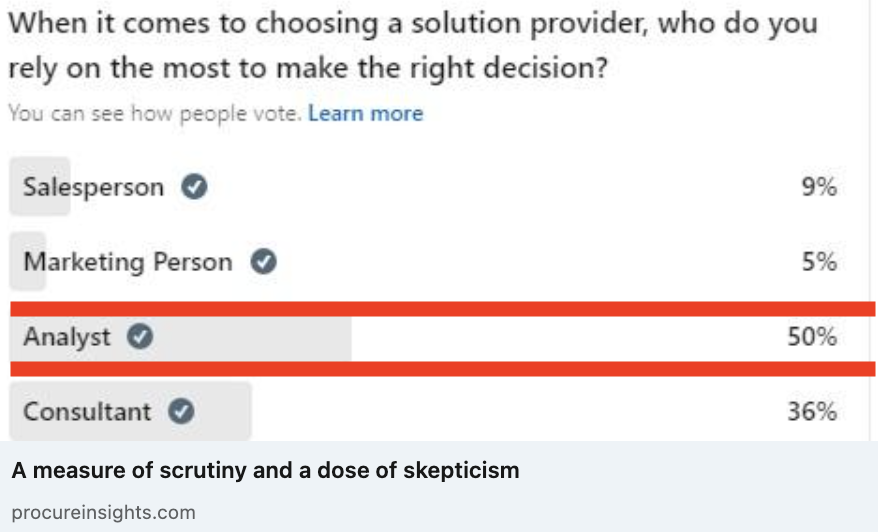
That’s right. Only 50% of practitioners trust analysts to help them make the right decision when selecting technology. 36% would rather a consultant, who likely has a very strong incentive to either recommend a preferred partner solution (where they are guaranteed to get the implementation contract) or the solution that requires the most implementation effort (to add months, or years, to the engagement), and, even worse, 14% would rather trust a marketer or salesperson, who gets paid for leads or sales, not for solving a customer’s problem!
As far as the doctor is concerned, anything less than 75% is appalling. While he will happily admit there are some independent consultants at smaller firms without vendor partnerships who will be truly objective and will offer valuable advice, this is not the norm at most of the larger firms that are preferred partners or implementation providers for the bigger players in our space (where the majority of consultants reside), so the fact that the consultant trust is so high is a little off-putting. However, he’s simply aghast at the fact that 14% would rather trust a salesperson or a marketer for solution advice. Frankly, this means we are definitely failing the market.
Basically, if we can’t be the unbiased experts and independent voices of reason that the Procurement practitioners can always trust for good, unbiased, advice, then what good are we?
So what can we do to regain the trust? the doctor is sad to say he’s not exactly sure and hopes that
- some other analysts will echo the call to action to deal with the PROCUREMENT STINK,
- analysts will collectively take the lead in cleaning it up and restoring our reputation, and
- offer up suggestions on what we can do to make it better!
Now, while the doctor doesn’t have all the answers, he does have suggestions on where we can start.
1. Be fully transparent on whom we do and don’t include in maps and logo charts, why, and the business situation in which our recommendations are, and are not, relevant.
This is quite obvious, and most of us are getting pretty good at being very explicit about the inclusion requirements for our maps and studies, but we don’t always take the time to clarify what this means for the market and, more specifically, which types of organizations the reports and maps are targeted at, which types of organizations will get the most value, and, most importantly, which types of organizations are unlikely to get any value because they don’t fall in the size/verticals/etc. the map or report is targeting. As far as the doctoris concerned, now more than ever we need to double down and get it right on both sides of the equation — who is being included, and why AND who should, and should not, be reading the report, and why, when we release something to the market. (Like the doctor did with his mega map.)
2. Stop glamourizing hype cycles and start busting them when there is no perceivable value to Procurement.
Procurement is supposed to be about solutions that deliver enterprise value, not cool technology. Leave that to the Consumer Electronics Show. When we promote tech for the sake of tech, we’re not helping anyone. We need to promote solutions to business problems with measurable ROI, regardless of what the underlying technology is. It’s irrelevant how many vendors embrace Gen-AI, when it has yet to demonstrate even a single use case that offers value beyond traditional tech, and the majority have failed to deliver any value.
3. Stop taking our cues from vendors as to where the space is going and start leading vendors to where the space should be going.
For example, intake-to-orchestrate is the craze, vendors are popping up faster than rabbits in a carrot field, and it’s likely only a matter of time before we see a map covering the intake-to-orchestrate space. (Especially since the doctor has been led to understand that one major analyst firm is already considering such a map, and where one leads, others will follow.)
However, in the doctor‘s view, this SHOULD NOT happen. Because, as stated above, and explained in detail in our article on why PROCUREMENT STINKS, there is NO VALUE in intake/orchestrate on its own. NONE. Intake is nothing more than pay-per-view on your data and orchestrate is just pure SaaS-based middleware, and middleware is something we’ve had for decades (and the need for such is negated completely if all the applications you use have complete, open, APIs as they can then be connected directly). The only value in these offerings would be in any additional functionality they embed to enhance the value of the applications they are linking together so that 1+1=3.
It would be understandable if they all embedded additional functionality that was comparable, valuable on its own, and formed a new application category that made sense to evaluate separately. However, right now, many don’t embed sufficient functionality; those that do are, for the most part, not comparable (as they all tend to specialize in something different, such as easy self-serve Procurement, services management, statements of work, etc.); and there has been no application thereof that wasn’t designed to enhance, or, most of the time, just make existing applications accessible. A standalone map would be senseless. (Instead, the intake and orchestrate requirements that are necessary for success should be included in the definition, and measurement of, Procurement, Sourcing, Supplier Management and other existing applications that can deliver enterprise value.)
3b. Start calling vendors out on bullsh!t when they start chasing, or putting, cool tech before practical solutions with actual ROI.
Privately at first (of course), unless the vendor insists on marketing it through a bullhorn. Then we may have no choice but to publicly call them out on it. Vendors may not like it, and may get upset when we burst their tech-centric bubble, but we’re not helping anyone when we don’t. Not us, not the procurement professionals we claim to support, and definitely not the vendors if we don’t try to dissuade them from throwing good money after bad on tech that won’t solve actual problems and ultimately won’t sell once their potential clients see the lack of value that comes with the price tag. This space has always been about ROI, we need to remind vendors of that, and guide them to where the ROI is just as we guide the practitioners. We need to be helpful to both sides to mature the space.
the doctor‘s not sure it’s enough, but it’s a start, and if other analysts make an effort to figure out how to restore our reputation, maybe we’ll find the answer, provide the unparalleled value that only we can provide, and get back the trust we should have.
Thoughts?
